Documentation & Downloads
Browse your product documentation including release notes and installers
The Community will be in read-only mode starting April 19th, 7:00 AM PDT. Check out the blog post!
You will still be able to use the case portal to create and interact with your support cases until the transition, view more information here!
- Carbon Black Community
- :
- Resources
- :
- Documentation & Downloads
- :
- Abuse.ch Feed Has Been Updated!
Abuse.ch Feed Has Been Updated!
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Abuse.ch Feed Has Been Updated!
Hello All!
We are pleased to announce that the Abuse.ch feed has been updated to provide broader and deeper coverage!
Product(s) Affected
- Cb Response
Deployment Date
- Thursday, 3/9/17
New Abuse.ch Feed Coverage
- Ransomware Tracker New!
- Feodo Tracker New!
- SSL Blacklist New!
- Zbot/ZeuS Tracker (Existing)
Required Customer Action(s)
- This will be a transparent update to the feed; if you have already enabled the feed there is no additional work needed.
Reminder
- We will apply these new capabilities retroactively (as well as in real time) so we will alert on previous activities that match the current indicators of malicious activity.
If you have any questions, please let us know!
Paul Riegle
Director, Product Management
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How to check if the Feed is enabled
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yay! Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Which Carbon Black product is this for?
Thanks,
Phylis Herrin
Application Administrator II
Cahaba Information Security
Phone: 205 220-1446
Email: pherrin@cahabagba.com<mailto:pherrin@cahabagba.com>
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Phylis,
This is for the Cb Response product - I've updated the announcement.
Thanks!
Paul
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
All,
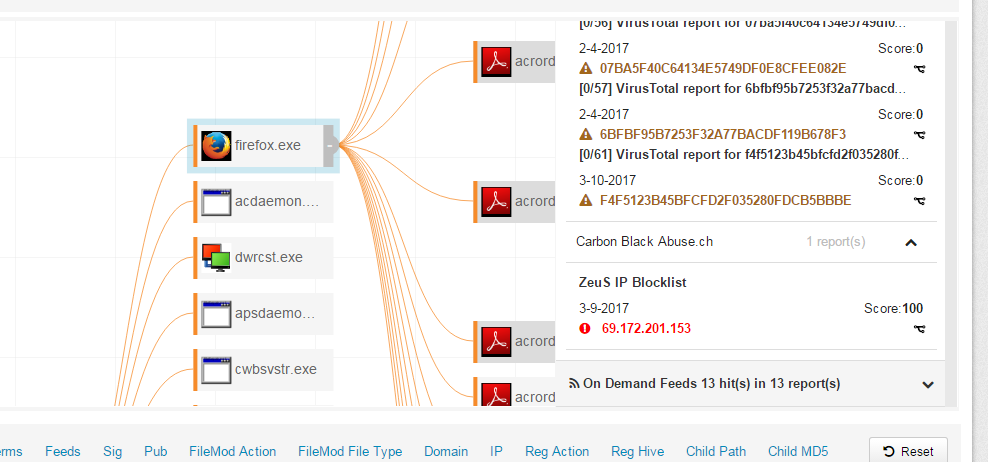
Since the Abusech updates came out, we have been seeing alerts for traffic to the IP 69.172.201.153. We are treating these as legitimate hits, but I am wondering if anyone else is running into it or has seen it? It is the ZeuS IP Blocklist from Abusech that is flagging it, which is concerning. Just wondering if anyone else is seeing it. Thanks.
Paul K.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm seeing the same thing for the IP 69.172.20.153. In looking it up in domain tools it appears that 2,510,954 websites use the address.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We are currently seeing a decent number of hits, and investigating.
That IP is definitely bad...
Will share if I learn more.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is not uncommon with IP based indicators, and is one of the reasons we spend more time investing in query based feeds that identify patterns of attack rather than static indicators. Sites that use shared hosting end up using the same IP addresses, and this IP is used by many, many sites (as mentioend by compl3tesle3t). I can confirm that there are sites hosted on that IP that are indeed owned/malicious (for example www[.]lafyeri[.]com), but obviously many/most of those sites hosted here are not compromised. Best bet is to look at the host in question, confirm that you are okay with the netconns you’re seeing within CbR, and then mark as a false positive.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
As an update to my previous comments - our hits to this IP are actually the result of a DNS suffix misconfiguration.
Fixing this issue - we can rule out 99% of this.
Hope this helps others.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes we got a hit on that one. I could not see anything strange associated with it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We have been seeing a lot of hits on this IP over the past week. We have found it associated to many different sites, but at this point have not seen any malicious activity on our network.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thank you for sharing the information .
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is a great addition, however we're observing a large number of false positives on the IP based indicators due to shared hosting.
Is there a way to keep IP data but only alert on Domains and Hash hits as they're higher fidelity? I don't want to lose the IP based data for enriching the logs...
It looks like there are only two options:
- Ignore the abuse.ch IP data feeds and continue alerting
- Turn off all alerting and only enrich data
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have seen more reports on abuse.ch but when I look at the events no such IP is found. Anyone else seeing this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is generating an alert everyday for binaries that were alerted from other threat feeds back in Nov 2018 and Jan 2019. Please check to see if the feed is operating nominally.
Thanks,
Gary
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.

