Knowledge Base
Access official resources from Carbon Black experts
Advanced Search
Threat Report: Exposing Malware in Linux-Based Multi-Cloud Environments | Download Now
- Carbon Black Community
- :
- Resources
- :
- Knowledge Base
- :
- Endpoint Standard: Why doesn't POLICY_DENY of KNOW...
Endpoint Standard: Why doesn't POLICY_DENY of KNOWN_MALWARE generate an Alert?
Options
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Endpoint Standard: Why doesn't POLICY_DENY of KNOWN_MALWARE generate an Alert?
Environment
- Carbon Black Cloud Console: All Versions
- Endpoint Standard (formerly CB Defense) Sensor: All Versions
- Microsoft Windows: All Supported Versions
- Apple macOS: All Supported Versions
Symptoms
- An Event in the Investigate Page of the CB Defense Web Console reports the following
The application C:\path\selectedapp.exe was prevented from accessing the file C:\path\targetapp.exe due to a Deny operation or Terminate process policy action. TTPS: POLICY_DENY and the target application has a KNOWN_MALWARE, SUSPECT_MALWARE, PUP, or COMPANY_BLACK_LIST reputation
- An Alert is not created for this event
Cause
If an application hash only attempts to do a generic READ access on the target malware then the sensor will block the action and log the event, but CB Defense will not form this event into an Alert.
Resolution
Depending on the policy rules in place, Endpoint Standard will prevent any application from accessing a known malware, suspect malware, pup, or company black list file. This behavior is effectively considered a file quarantine or "quarantine-in-place". The read operation will be denied, logged, and provisionally included in any threat that may be created at that time if one or more of the minimum criteria is met:
- Endpoint Standard Sensor first detects the malware on the local disk either from background scan or when the malware is initially created or dropped
- Another application attempts to READ malware with the intention to EXECUTE or RUN the malware
- The malware process was already running and the Endpoint Standard Sensor terminates the process
- Event data is sent from the Sensor to the backend and analyzed to determine whether an AlertID should be assigned to the Event
- If an AlertID is assigned, the Event will be categorized as either a Threat or Monitored Alert and shown on the Alerts page
Additional Notes
- The reason for this behavior is to reduce excessive or repetitious Alerts on read access of malware.
- This could happen when backup software or disk indexing performs continuous READ operations of the malware file.
- Even without the presence of such software, continuous read operations may occur every time the end user opens the file directory or path that contain the malware. This is especially true in cases where an environment is already inundated with newly downloaded or commodity malware which existed on these devices prior to the Endpoint Standard Sensor being installed.
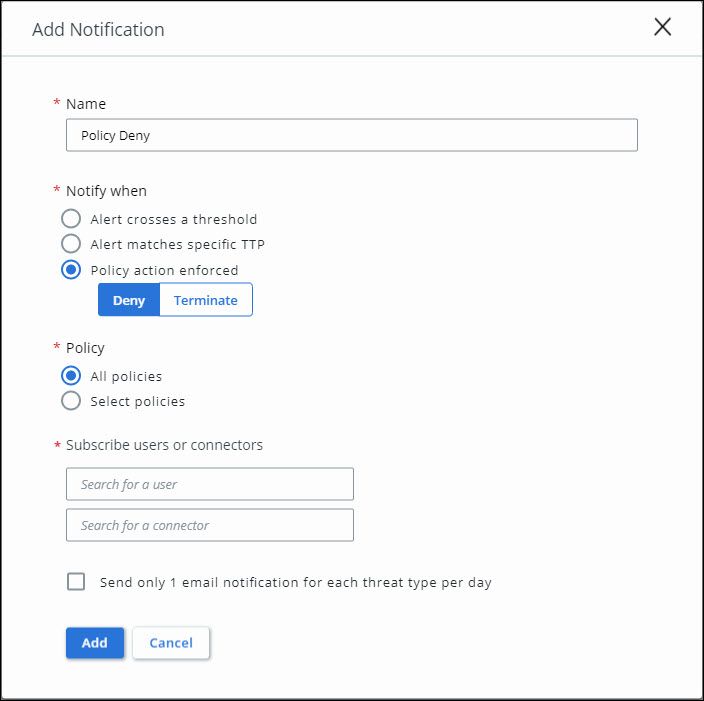
- If a notification on every deny event is required, please create a notification in the Carbon Black Cloud Console to notify when Policy action enforced: Deny
- If notifications based for when Alert crosses a threshold (THREAT, MONITORED, Alert Priority) exist, duplicate notifications for the same event may be received if a policy action is also enforced.
Related Content
Cb Defense: Severity, Threat Level, Target Value, Malware Types Information
Cb Defense: How to Delete Malicious Files through the Dashboard
Cb Defense: How To Provide A Malware Sample To Carbon Black Support
Cb Defense: How to Delete Malicious Files through the Dashboard
Cb Defense: How To Provide A Malware Sample To Carbon Black Support
100% helpful
(3/3)
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.
Thank you for your feedback.
Your feedback has been submitted and will be reviewed.
Thank you for your feedback.
Valid.
Please fill out this
field.
InValid.
Please fill out valid email.
Valid.
Please fill out this
field.
Please do not send sensitive data through this form
Valid.
Please fill out this
field.
Description length should be less 30K