Knowledge Base
Access official resources from Carbon Black experts
The Community will be in read-only mode starting April 19th, 7:00 AM PDT. Check out the blog post!
You will still be able to use the case portal to create and interact with your support cases until the transition, view more information here!
- Carbon Black Community
- :
- Resources
- :
- Knowledge Base
- :
- Cb Defense: Windows 10 Apps that require (UAC) per...
Cb Defense: Windows 10 Apps that require (UAC) permissions are crashing
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Cb Defense: Windows 10 Apps that require (UAC) permissions are crashing
Environment
- Cb Defense Sensor: All Versions
- Microsoft Windows: Windows 10 1703 build 15063 (Creators Update) and lower
Symptoms
- Windows 10 applications that require Windows User Account Control (UAC) will not run.
- Windows Application Event Log shows that both the application (In this example it is mmc.exe) and consent.exe are crashing.
Application Error 1000 (100) "Faulting application name: mmc.exe, version: 10.0.15063.0, time stamp: 0xc39bfa6e
Faulting module name: unknown, version: 0.0.0.0, time stamp: 0x00000000
Exception code: 0xc0000409
Fault offset: 0x0000000000000000
Faulting process id: 0x11bc
Faulting application start time: 0x01d3ac1ec273770c
Faulting application path: C:\WINDOWS\system32\mmc.exe
Application Error 1000 (100) "Faulting application name: consent.exe, version: 10.0.15063.0, time stamp: 0xe0f856c4
Faulting module name: unknown, version: 0.0.0.0, time stamp: 0x00000000
Exception code: 0xc0000409
Exception code: 0xc0000409
Fault offset: 0x0000000000000000
Faulting process id: 0x1798
Faulting application start time: 0x01d3ac1eb5fd3cca
Faulting application path: c:\windows\system32\consent.exe
Cause
This issue occurs because Windows prevents the Cb Defense Sensor from injecting it's apphook, ctiuser.dll, into the application requesting administrator access and the UAC process, consent.exe.
Resolution
- To resolve this issue, please upgrade to Windows 10 version 1709 build 16299 (Fall Creators Update).
If you are unable to upgrade to the Fall Creators update, then as a workaround you can also create an API Bypass rule for the UAC process, consent.exe and the application(s) that typically require UAC access such as mmc.exe. To add an api bypass rule for each application in the Cb Defense Web Console go to Policies, Select your Policy and select ADD APPLICATION PATH.
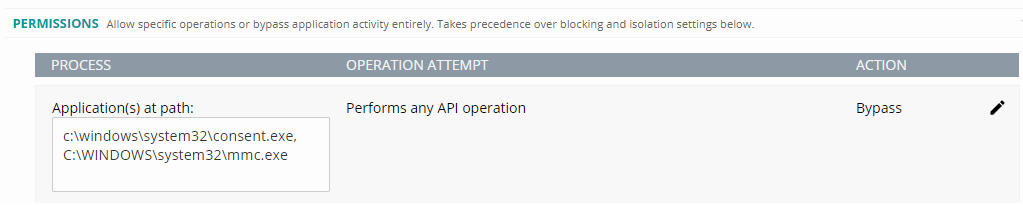
Additional Notes
- For complete visibility into all application actions, the Cb Defense sensor must perform a full apphook injection into the application.
- By configuring a permissions rule to bypass the application path when action "Performs any API operation", you can address interoperability issues with any third-party applications that have performance issues when Cb Defense preventions are enabled. This is because the Cb Defense apphook only performs a partial injection into the application process. This permissions rule lets those applications execute, but prevents Cb Defense from enforcing preventions for the following policy operations due to limited apphook injection.
- Tries to scrape memory
- Tries to inject code
- Tries to execute code from memory
- Master Boot Record protection for Performs ransomware-like behavior
Related Content
How User Account Control works
Cb Defense: How to Utilize Bypass Mode
Cb Defense: Troubleshooting Performance and Interop Issues with the Sensor
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.

