Documentation & Downloads
Browse your product documentation including release notes and installers
The Community will be in read-only mode starting April 19th, 7:00 AM PDT. Check out the blog post!
You will still be able to use the case portal to create and interact with your support cases until the transition, view more information here!
- Carbon Black Community
- :
- Resources
- :
- Documentation & Downloads
- :
- PSC Release Notes May 2019
PSC Release Notes May 2019
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
PSC Release Notes May 2019
This May 2019 release notes article contains information about the following releases:
CB Defense
Delete a file from the Alert Triage page
You can now delete a file from the Alert Triage page. Selecting a file provides details on the file, and the ability to take action on it.
CB ThreatHunter
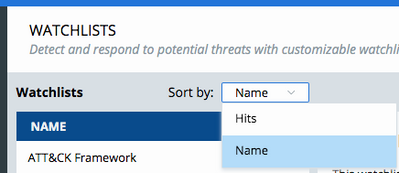
Sort order on Watchlists page persists
When you change the sort order on the Watchlists page, that setting persists across sessions in the same browser.
Investigate page improvements
When you start a search by first selecting a filter option, and then add query terms to the Search Bar, the resulting search results now honor the filter selections as well as Search Bar terms.
The Device Group filter category has been renamed to Policy, to better represent the data upon which it acts.
Fixed in this release
|
Issue ID |
Description |
|
DSER-14269 |
On the Watchlists page and related screens, when you select a checkbox and take action such as Add or Subscribe, the checkboxes remain selected after the action is successfully completed. |
|
DSER-16076 |
Investigate search results sometimes include exact duplicate results in pairs. |
|
DSER-16099 |
Process Analysis tree shows only one node. |
|
DSER-13061 |
In the Feed Manager Replace Reports API, the response included a 500 HTTP status code when it should be 400. |
|
DSER-14988 |
Report tags were incomplete for some third-party Watchlists. |
Known issues
|
Issue ID |
Description |
|
TPLAT-6201 |
The First seen as field on the Binary Details page (and from the API) does not return paths in prevalence order; therefore, it is not possible to guarantee the actual first seen instance. |
|
DSER-10685 |
Text remains in Investigate Search Bar if user navigates away and uses navigation Investigate option return to the Investigate page. |
|
DSER-11445 |
Hovering the mouse on a Investigate search filter hides the percentage values. |
|
DSER-11662 |
After you deselect a selected filter on the Investigate page, an otherwise-empty search still displays search results. |
|
DSER-11904 |
Count of devices with hash on the Process Analysis page is different from count of devices on the Investigate page. |
|
DSER-11959 |
When user types - or + and then accepts a suggested search field name, the + or - character is removed from the search bar on the Investigate page. |
|
DSER-12453 |
ThreatHunter Watchlist tags do not show up on the Notes/Tags tab of the Alerts page — these are a different type of tag data. |
|
DSER-12538 |
Binary Details page crashes when UBS APIs return unexpected output. |
|
DSER-13177 |
The User Guide is missing from the Help menu for organizations that subscribe to CB ThreatHunter. |
|
DSER-13271 |
No field descriptions/examples in many suggestions for search fields on Process Analysis page. |
|
DSER-13283 |
When you search for Reports for a new Watchlist, you cannot access or add a Report that was returned by the search. |
|
DSER-13295 |
For processes that have a very large number of events, the Process Analysis page for that process can be manually reloaded to load additional events until the query is completed in the background. |
|
DSER-13636 |
Facets do not update when you navigate away from the Investigate page and then navigate back. |
|
DSER-13773 |
Watchlist link still showing on Process Analysis page side panel after Watchlist is deleted. |
|
DSER-14090 |
If CB Defense is enabled on the PSC with WSC integration enabled, and you remove CB Defense, the WSC integration is not disabled. |
|
DSER-14148 |
When Investigate search bar overflows to multiple lines, user cannot use keyboard navigation or selection. |
|
DSER-14276 |
When user deletes a custom Watchlist from enabled Watchlists page, results section of page reports "no watchlists enabled". |
|
DSER-14758 |
Searching by device_internal_ip returns no results for CBTH-native events on the Investigate page. |
|
DSER-14764 |
For an organization that only uses ThreatHunter, the CB Defense icon still appears in the Explorer tray and the Programs List. |
|
DSER-14832 |
When there is only one device_group available, the /results API does not return device_group and the Device Group filter group disappears from the Investigate page. |
|
DSER-15013 |
Rule Preview links show inconsistent result counts when you use wildcards on the Policies page. |
|
DSER-15052 |
More Watchlist Notification emails sent than number of Watchlist Hits or Alerts. |
|
DSER-15187 |
"process_publisher" searches on the Investigate page lead to signed and unsigned binaries. |
|
DSER-15385 |
Result count drops and rises when changing filters or terms on Investigate search. |
|
DSER-15386 |
When user deletes the last Report in an enabled Watchlist, the Reports tab on Watchlists page shows all available reports instead of No Reports for this Watchlist. |
|
DSER-15931 |
Report Search on Watchlists page allows user to submit search when Search Bar is empty. |
|
DSER-16080 |
Report Search on Watchlists page returns a 500 error when querying for more than 10,000 reports. |
|
DSER-16083 |
On the Watchlists page, the backspace key does not behave as expected to edit a Watchlist name or description |
|
DSER-16084 |
In the Update Watchlist API, an empty Name field is allowed. |
|
DSER-16087 |
In the Create New Report API, the API responds with 500 error if a negative timestamp is submitted |
|
DSER-16190 |
The device_policy field is not always populated in API data or Investigate filters |
CB Defense
This release includes an improvement to our database connection pool settings, which should result in increased stability.
CB Defense
Fixed in this release
|
Issue ID |
Description |
|
DSER-15875 |
Fixed an issue where upgrading to Chrome v74 caused the Roles page to crash. |
|
DSER-15708 |
Fixed an issue where the Prevent with Policies section of Getting Started appeared when it did not apply to the active products. |
CB ThreatHunter
Fixed in this release
|
Issue ID |
Description |
|
DSER-15386 |
When user deleted the last Report in an enabled Watchlist, the Reports tab showed all available Reports rather than No Reports for this Watchlist. |
|
DSER-15821 |
Add Watchlists Build Tab: Could not add Threat Report to Watchlist. |
|
DSER-15822 |
Syntax highlighting for modload_hash field highlighted incorrectly. |
|
DSER-15861 |
Viewing Watchlist With No Reports showed ALL Reports. |
Known issues
|
ID |
Description |
|
TPLAT-6201 |
First seen as field on the Binary Details page (and from the API) does not return paths in prevalence order; therefore, it is not possible to guarantee the actual first seen instance. |
|
DSER-10685 |
Text remains in Investigate search bar if user navigates away and uses navigation Investigate option return to the Investigate page. |
|
DSER-11445 |
Hovering the mouse on a Investigate search filter hides the percentage values. |
|
DSER-11662 |
After you deselect a selected filter on the Investigate page, an otherwise-empty search still displays search results. |
|
DSER-11904 |
Count of devices with hash on the Process Analysis page is different than count of devices on the Investigate page. |
|
DSER-11959 |
When user types - or + and then accepts a suggested search field name, the + or - character is removed from search bar on the Investigate page. |
|
DSER-12453 |
ThreatHunter Watchlist tags do not show up on the Notes/Tags tab of the Alerts page — these are a different type of tag data. |
|
DSER-12538 |
Binary Details page crashes when UBS APIs return unexpected output. |
|
DSER-13061 |
Feed API "replace reports" API call responds with 500 when it should send 400. |
|
DSER-13177 |
The User Guide is missing from the Help menu for organizations that subscribe to CB ThreatHunter. |
|
DSER-13271 |
No field descriptions/examples in many suggestions for search fields on Process Analysis page. |
|
DSER-13283 |
When you search for Reports for a new Watchlist, you cannot access/add a Report that was returned by the search. |
|
DSER-13295 |
For processes that have a very large number of events, the Process Analysis page for that process can be manually reloaded to load additional events until the query is completed in the background. |
|
DSER-13636 |
Facets do not update when you navigate away from the Investigate page and then navigate back. |
|
DSER-13773 |
Watchlist link still showing on Process Analysis page side panel after Watchlist is deleted. |
|
DSER-14090 |
If CB Defense is enabled on the PSC with WSC integration enabled, and you remove CB Defense, the WSC integration is not disabled. |
|
DSER-14148 |
When Investigate search bar overflows to multiple lines, user cannot use keyboard navigation or selection. |
|
DSER-14276 |
When user deletes a custom Watchlist from enabled Watchlists page, results section of page reports "no watchlists enabled". |
|
DSER-14758 |
Searching by device_internal_ip returns no results for CBTH-native events on the Investigate page. |
|
DSER-14764 |
For an organization that only uses ThreatHunter, the CB Defense icon still appears in the Explorer tray and the Programs List. |
|
DSER-14832 |
When there is only one device_group available, the /results API does not return device_group and the Device Group filter group disappears from the Investigate page. |
|
DSER-15013 |
Rule Preview links show inconsistent result counts when you use wildcards on the Policies page. |
|
DSER-15052 |
More Watchlist Notification emails sent than number of Watchlist Hits or Alerts. |
|
DSER-15187 |
"process_publisher" searches on the Investigate page lead to signed and unsigned binaries. |
|
DSER-15385 |
Result count drops and rises when changing filters or terms on Investigate search. |
|
DSER-15386 |
When user deletes the last Report in an enabled Watchlist, the Reports tab on Watchlists page shows all available reports rather than No Reports for this Watchlist. |
|
DSER-15931 |
Report Search on Watchlists page allows user to submit search when Search Bar is empty. |
Our May 6 release of the PSC extends and improves recently released features, making visibility and prevention faster and easier.
- In April 2019, Carbon Black released CB LiveOps recommended queries, a set of pre-built queries that are recommended by the Carbon Black threat research team. Now, you can filter recommended queries based on operating system and categories, including compliance, IT hygiene, threat hunting, and vulnerability management.
- In April 2019, CB ThreatHunter search became more flexible, enabling users to search without specifying field names.
- In March 2019, we introduced role-based access control (RBAC) capabilities across the PSC to give administrators granular control over user roles. In this release, we’re making it even easier to view all available roles. We’re also extending the Getting Started dashboard widget to help CB Defense users learn how to create, assign, test, and tune policies.
For more information about other recently added CB Defense and CB LiveOps features, see the April 24 PSC Release Notes.
CB Defense
Connectors renamed to API Keys
Based on customer requests, all “Connector” related terminology is updated to “API Key” terms. For example:
- The Connectors page has been renamed to API Keys.
- Connector Type is now referred to as API Key Access Level.
- The API Key button that revealed the secret key is renamed to Credentials and shows both the ID and the Key.
- API keys include 2 parts: API Secret Key (previously API Key) and API ID (previously Connector ID).
Getting started with policies
The Getting Started widget can help you Prevent with policies. If you are unfamiliar with policies, four new steps can help you set up, assign, and test new policies.
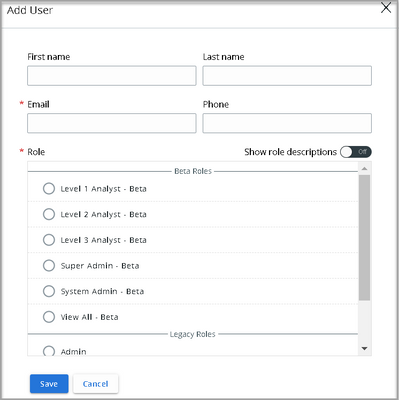
New user assignment design
The Users page Add User window is redesigned to more easily browse through available roles. The new view shows all the roles within a scrollable window. By toggling Show Role Descriptions, you can review and compare multiple role descriptions simultaneously.
Improved Audit Log messages
Audit Log messages related to API Keys are updated to include the API IDs that were used, and the orgId of which they are a part. These changes make it easier to identify what API Keys were modified. Example messages:
- Deleted API ID ABCD7MUZWJ in org 12345
- Added API ID ABCD7MUZWJ with name test-notifications in org 12345
- User test@example.com retrieved secret key for API ID ABCD7MUZWJ in org 12345
Detection analytics improvements
In a continued effort to improve detection analytics, new detection capabilities and false positive reduction fixes have been added. In this release, we focused primarily on attacks that leverage native Windows applications to perform malicious activity. Additionally, we focused on reducing high-impact false positives related to code injection and port scanning activities. You should see improved detection capability in the Alerts page.
Please see the following list of improvements:
|
Type |
Name |
Description |
|
New Detection |
Microsoft Office Apps Invoking Script Hosts |
Improved detection capability for Microsoft Office applications that invoke Powershell and other script hosts, by re-categorizing and elevating the score of these alerts and thereby making them more prominent. |
|
New Detection |
Mavinject Injection Malicious Code |
Improved detection of attackers that leverage Mavinject, a native signed Windows application, to inject malicious code into other applications. |
|
New Detection |
MSBuild Making Network Connections |
Improved detection of attackers that leverage MSBuild, a native signed Windows application, to make malicious network connections to other devices. |
|
New Detection |
Constructing Applications on the Fly |
Improved detection of attackers that leverage native Windows tools to download and construct malicious applications from the Internet in an attempt to evade standard detection techniques. |
|
New Detection |
Credential Theft |
Improved ability for analytics to detect attempted credential theft that evades standard Windows security policy enforcement. |
|
False Positive Reduction |
Code Injection |
Eliminated alerts related to uncompromised Windows services that inject code into email applications that are known to not be suspicious. |
|
False Positive Reduction |
Code Injection |
Eliminated alerts related to uncompromised Windows services that inject code into custom, whitelisted Office applications that are known to not be suspicious. |
|
False Positive Reduction |
Port Scanning |
Eliminated alerts related to a common network security application that is known to scan local networks to verify connecting devices. |
Fixed in this release
|
Issue ID |
Description |
|
DSER-15293 |
Fixed an issue where a role that had the Manage Devices permission could not access the Endpoints page’s Send Installation Request button. |
|
DSER-15077 |
Fixed an issue where the UI gave the impression that a user’s email address could be changed after account creation. |
|
DSER-15073 |
Fixed an issue where resetting 2FA for a user actually reset the user trying to do the reset. |
|
DSER-14828 |
Fixed an issue where initializing a Live Response session did not set an expiration time, resulting in hung sessions when no command was issued. |
|
DSER-8931 |
Fixed an issue where users could not add or delete tags for an alert. |
Known issues
|
ID |
Description |
|
DSER-4390 |
Some sensors that should be Eligible for Upgrade are not marked as such. |
|
DSER-5437 |
Additional markup is added to events forwarded via the event forwarder. |
|
DSER-9664 |
Occasionally, clicking the link on an emailed alert notification results in the Alert Triage page not rendering correctly. |
|
DSER-9670 |
Searching for “Threat Category: Malware” on the Alerts page returns results that are non-malware. |
|
DSER-10342 |
Selecting Take Action > Uninstall from the Endpoints page fails to uninstall sensors in some cases. This leaves the sensor installed on an endpoint, but unable to communicate with the cloud. |
|
DSER-10667 |
When an application's reputation is first determined to be NOT_LISTED and is then whitelisted, events shows WHITE_LISTED on the Investigate page. The application still shows as NOT_LISTED in the Applications tab. |
|
DSER-10714 |
An incorrect API URL is listed on Settings > API Keys > Download. Please see this KB for the proper URLs: https://community.carbonblack.com/t5/Knowledge-Base/CB-Defense-What-URLs-are-used-to-access-the-API/.... |
|
DSER-10961 |
Older macOS sensor versions allow deletion of sensor files from the backend. This can occur on macOS sensor versions 3.1 and lower. This only occurs if an org administrator manually triggers the deletion. |
|
DSER-11370 |
If an alert dismissal reason is selected when dismissing an alert, the alert does not dismiss properly. |
|
DSER-12676 |
A notification for an alert can be sent when dismissing an alert, causing duplicate notifications to appear. |
|
DSER-12728 |
In rare situations, navigating to some pages in the UI causes the page to render as gray. Refresh the page to render the page as expected. |
|
DSER-13914 |
Auto-delete of deregistered devices is not functioning properly. Manual deregistration is working as expected. |
|
DSER-14906 |
When using the /device/all?fileformat=xyz API to export all devices, deleted devices are incorrectly included in the export. |
CB ThreatHunter
Renamed reputation fields on Events API
For requests to the Event search API endpoint (/threathunter/search/v1/orgs/{{org_key}}/events/_search), the reputation fields were incorrectly named. We have updated these field names as follows:
|
Previous field name |
Current field name |
|
modload_reputation |
modload_effective_reputation |
|
scriptload_reputation |
scriptload_effective_reputation |
|
crossproc_reputation |
crossproc_effective_reputation |
|
childproc_reputation |
childproc_effective_reputation |
Note: No other fields are being renamed at this time.
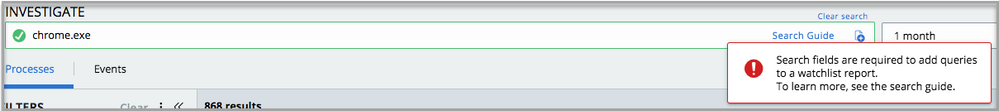
IOCs must include field-qualified search parameters when being added to a Watchlist
When adding an IOC to a new or existing Watchlist via the Investigate page, the PSC requires all search parameters to be qualified with an explicit field.
Failure:
Success:
New ThreatHunter API versions
Updated the following APIs:
- Feed Manager updated to v2.
- Process Search updated to v1.
- Watchlists updated to v3.
API documentation is available on our Developers Website.
Also in this release
- On the Watchlists page, you can sort by Severity on the Hits tab.
- The alert_id field on Investigate search now includes both types of Alerts — those from CB Analytics and those from Watchlists.
- Investigate search now allows you to search by name of your CB ThreatHunter Watchlist, using the new watchlist_name field.
Fixed in this release
|
Issue ID |
Description |
|
DSER-13337 |
Threat Reports were deleted but still appeared in the Watchlist Details API response. |
|
DSER-14731 |
Watchlist Description field was required by API but not in UI (now not required). |
For information about other recently fixed issues, see the April 15 and April 29 PSC Release Notes.
Known issues
|
ID |
Description |
|
TPLAT-6201 |
First seen as field on the Binary Details page (and from the API) does not return paths in prevalence order; therefore, it is not possible to guarantee the actual first seen instance. |
|
DSER-10685 |
Text remains in Investigate search bar if user navigates away and uses navigation Investigate option return to the Investigate page. |
|
DSER-11445 |
Hovering the mouse on a Investigate search filter hides the percentage values. |
|
DSER-11662 |
After you deselect a selected filter on the Investigate page, an otherwise-empty search still displays search results. |
|
DSER-11904 |
Count of devices with hash on the Process Analysis page, is different than count of devices on the Investigate page. |
|
DSER-11959 |
When user types "-" or "+" then accepts a suggested search field name, the + or - character is removed from search bar on the Investigate page. |
|
DSER-12453 |
ThreatHunter Watchlist tags do not show up on the Notes/Tags tab of the Alerts page — these are a different type of tag data. |
|
DSER-12538 |
Binary Details page crashes when UBS APIs return unexpected output. |
|
DSER-13061 |
Feed API "replace reports" API call responds with 500 when it should send 400. |
|
DSER-13177 |
The User Guide is missing from the Help menu for organizations that subscribe to CB ThreatHunter. |
|
DSER-13271 |
No field descriptions/examples in many suggestions for search fields on Process Analysis page. |
|
DSER-13283 |
When you search for Reports for a new Watchlist, you cannot access/add a Report that was returned by the search. |
|
DSER-13295 |
For processes that have a very large number of events, the Process Analysis page for that process can be manually reloaded to load additional events until the query is completed in the background. |
|
DSER-13636 |
Filters do not update when you navigate away from the Investigate page and then navigate back. |
|
DSER-13773 |
Watchlist link still show on the Process Analysis page side panel after the Watchlist is deleted. |
|
DSER-14090 |
If CB Defense is enabled on the PSC with WSC integration enabled, and you remove CB Defense, the WSC integration is not disabled. |
|
DSER-14148 |
When the Investigate search bar overflows to multiple lines, you cannot use keyboard navigation or selection. |
|
DSER-14276 |
When you delete a custom Watchlist from an enabled Watchlists page, results section of page reports "no watchlists enabled". |
|
DSER-14758 |
Searching by device_internal_ip returns no results for CB ThreatHunter-native events on the Investigate page. |
|
DSER-14764 |
For an organization that only uses CB ThreatHunter, the CB Defense icon still appears in the Explorer tray and the Programs List. |
|
DSER-14832 |
When only one device_group is available, the /results API does not return device_group and the Device Group filter group disappears from the Investigate page. |
|
DSER-15013 |
Rule Preview links show inconsistent result counts when you use wildcards on the Policies page. |
|
DSER-15052 |
More Watchlist Notification emails are sent than the number of Watchlist Hits or Alerts. |
|
DSER-15081 |
In some cases, script load events are reported as process creation events. |
|
DSER-15187 |
"process_publisher" searches on the Investigate page lead to signed and unsigned binaries. |
|
DSER-15385 |
Result count drops and rises when changing filters or terms on Investigate search. |
|
DSER-15386 |
When user deletes the last Report in an enabled Watchlist, the Reports tab on Watchlists page shows all available reports rather than "No Reports for this Watchlist". |
|
DSER-15532 |
Starting a search on the Process Analysis page with a hyphen-prefixed field name yields no results. |
|
DSER-15704 |
Configurable filters on Investigate page do not persist after a user signs out. |
|
DSER-15767 |
When an organization has no recent data, the Watchlists page submits a red toast error. |
|
DSER-15784 |
ThreatHunter searches that send parameter data with the wrong type cause 502 Bad Gateway error. |
|
DSER-15805 |
Add Query to Watchlist on Investigate page while selecting the Include historical data checkbox causes "Error while creating IOC"; but the Watchlist is still created. |
|
DSER-15821 |
Add Watchlists Build tab: Cannot add Threat Report to Watchlist. When adding Threat Report to Watchlist fails, Watchlist is created with no Reports, and shows all Reports (due to DSER-15861). |
|
DSER-15822 |
Syntax highlighting for modload_hash field highlights incorrectly. |
|
DSER-15861 |
Viewing Watchlist with no Reports shows all Reports. |
CB LiveOps
Fixed in this release
|
Issue ID |
Description |
|
DSER-14609 |
UI inconsistencies on the Query Builder |
For information about other recently fixed issues, see the April 29 PSC Release Notes.
To print: Click the Show options menu (3 vertical dots next to the article), click Printer Friendly Page, right-click the page, and then click Print.
Carbon Black, Inc. | 1100 Winter Street, Waltham, MA 02451 USA | Tel: 617.393.7400
Copyright © 2011–2019 Carbon Black, Inc. All rights reserved. Carbon Black, CB Defense, CB LiveOps, CB ThreatSight, and CB ThreatHunter are registered trademarks and/or trademarks of Carbon Black, Inc. in the U.S. and/or other countries. All other trademarks and registered trademarks are the property of their respective owners.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can I get PDF document?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @yukisato -- I don't know if they plan on making the release notes available as a PDF, but if you go to the link below and use the print function from your browser you should have the option to save off the doc as a PDF before printing.
Let me know if you have any issues.
https://community.carbonblack.com/t5/tkb/articleprintpage/tkb-id/product-docs-news/article-id/2132
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.